Managing software licenses is a critical yet often overlooked aspect of IT operations. With the increasing reliance on various software solutions, keeping track of licenses, renewals, and compliance can quickly become overwhelming. Missing a due date for software license renewals can lead to costly consequences, including software downtime, compliance issues, and even legal penalties. However, […]
Author: Michelle

What is a Medical Computer?
VITA KW22 by AlexKT on Sketchfab VITA KW22 by AlexKT on Sketchfab https://blog.tangent.com/wp-content/uploads/2024/08/1.jpg Wondering what a medical computer is? In the healthcare industry, technology plays a crucial role in delivering patient care. From managing patient records and tracking medication orders to performing diagnostic tests and supporting telemedicine, healthcare professionals rely on computers and digital devices […]

What is Software License Management?
Software licensing management is the practice of monitoring, documenting, and ensuring the proper use of software licenses within an organization. This process is crucial for both software vendors and users to ensure compliance, optimize software utilization, and avoid legal and financial penalties. Key Aspects of Software Licensing Management Types of Software Licenses Perpetual Licenses: Purchased […]

Cubes Software License Management
Software license management solutions offer a centralized repository to view your organization’s multiple licenses, their cost, and due dates. It makes for what could be a murky situation, into an easy to view and manage workflow. Within organizations, there is typically an admin responsible for paying for software licenses, keeping track of their expense and […]

Prevent Corporate E-Mail Spoofing and Spam with DMARC Director
Email is a cornerstone of corporate communication, however, this essential tool is frequently targeted by cybercriminals through methods such as email spoofing and spamming. Corporate email spoofing involves sending emails that appear to be from a legitimate source but are actually from an attacker. This method is used to trick recipients into divulging sensitive information, […]

Why Your Business Needs a Software License Management Tool NOW
Unused software licenses can lead to unnecessary IT spending, a common issue in many IT organizations. Without proper records or systematic tracking, finances can slip through the cracks unnoticed. Inefficient license management results in non-compliance and hefty fines. Cubes helps organizations record and manage software licenses, significantly reducing unwanted IT spending and ensuring audit-readiness. 3 […]

Maximize the Power of Microsoft Office 365 with eLearning
As a Microsoft Gold Partner, it’s vital that our clients understand the full use of their MS business solutions. Online training for Microsoft Office 365 is available, and it’s called eLearning. You can watch videos and learn how to use each MS Suite conveniently from Teams. Alternatively, how about having how-to guides or guided learning […]
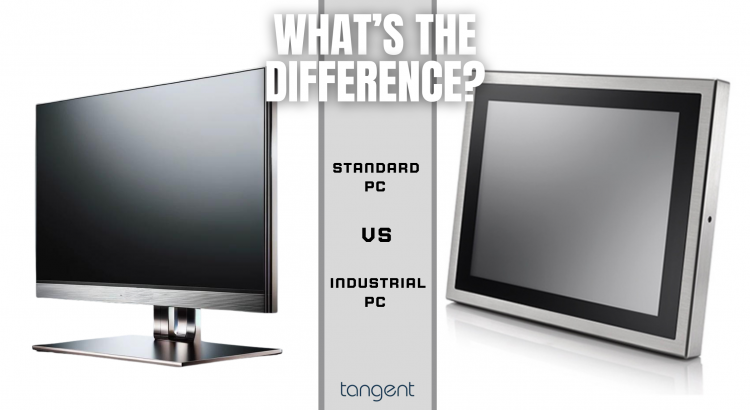
What is the Difference between Industrial PC and a Normal PC?
Industrial PCs vs. Standard PCs: A Detailed Comparison Industrial PCs and normal PCs can be compared to racecars and standard cars. While both are vehicles designed for transportation, one is highly specialized and purpose-built for high-performance on the speedway. Similarly, both industrial PCs and normal PCs are computers, but they serve very different purposes. Normal […]

CoPilot for Microsoft 365
AI has revolutionized the way we approach the workplace. Through automation of routine tasks, AI reduces the burden on employees, allowing them to focus on more strategic and creative endeavors. AI contributions include enhanced productivity, streamlining processes, and fostering innovation. For organizations already leveraging Microsoft 365, the value of Microsoft’s suite of tools is clear […]

What Does a Software License Manager do?
Software License Managers allow you to Manage, track, and maintain license information—all with one tool Who has the time to stay updated with every application, software program, and digital platform used in your organization? Cubes can assist. Cubes software license management solution is designed to centralize all license information, billing management, alerts and renewals. Cubes […]
